What is that for and what is the need ?
Philippe Guedez and I had the need to highly secure the access of a Web application that was developed on Microsoft Azure. To do so, we have used the Azure Multi-Factor Authentication (MFA) as part of the AAD (Azure Active Directory).
Not only the login page is going to ask you your login/password as usual, it is going to send you a text message on your mobile phone with an additional code. You could also configure MFA to use other secure ways to authenticate.
If you have an application, with a tenant id of say, 1477db05-0f2c-8924-904b-c87e8f0e928f, you’ll access to your configuration page by the following actions, which leads you to the URL (for example): https://account.activedirectory.windowsazure.com/usermanagement/multifactorverification.aspx?tenantid=1477db05-0f2c-8924-904b-c87e8f0e928f&culture=en-US
MFA will enforce compliancy to rules and regulations that requires high auditing standards, such as NIST 800-63 level 3, HIPAA, PCI DSS.
The various steps:
STEP 1 : ACTIVATING MFA
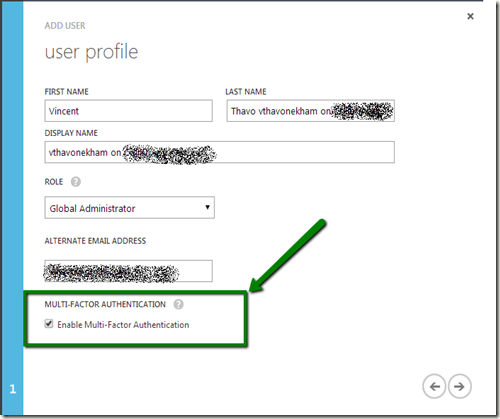
STEP 2 : ADD NEW MFA USER AND PASSWORD
STEP 3 : LETS CONFIGURE THE ACCOUNT AS A NEW USER RECEIVING THE EMAIL
STEP 4 : LET’S use the multi-factor authentication that is going to send me a text message
APPENDIX 1 : Windows Azure MFA Admin portal (formally PhoneFactor)
APPENDIX 2 : ALTERNATIVES: OLD FASHION RSA-SecurID way
You could activate MFA for Azure or for Office 365: http://blogs.technet.com/b/ad/archive/2014/02/11/mfa-for-office-365-and-mfa-for-azure.aspx
=====================
You could exclude the constraints of MFA when the user is within the company given an IP range (it is in preview) :
The various roles that you could filter by:
To enable MFA:
STEP 2 : ADD NEW MFA USER AND PASSWORD
You could add new users by activating the “Enable Multi-Factor Authentication” option.
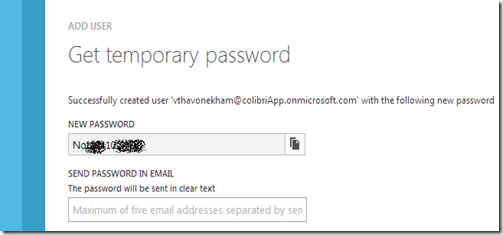
Provide an email so that the end user could receive this temporary password, for first login.
STEP 3 : LETS CONFIGURE THE ACCOUNT AS A NEW USER RECEIVING THE EMAIL
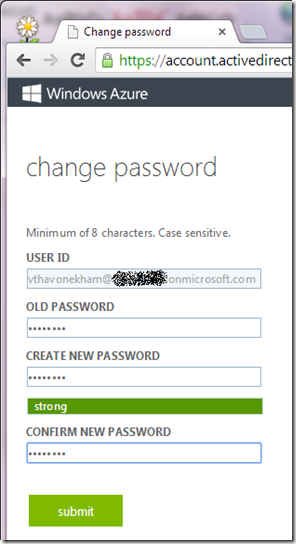
Enter the new account (use your temporary password):
Then, you’ll be forced to choose a proper and strong password
Set-up the MFA that will use, for instance Mobile phones:
If you really don’t know what to do, you have a video to help you: http://channel9.msdn.com/posts/Multi-Factor-Account-Setup

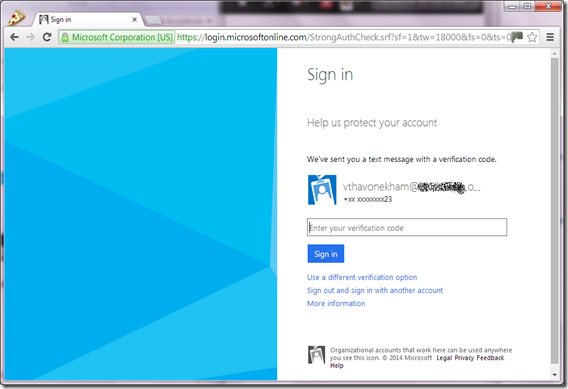
Instantaneously, you will receive a text message “your Microsoft sign in verification code is above. Type this code into your application to continue.” with your code.
If you wait too long like me, when writing this blog! you’ll get this error message and ask you to resend a text message
So let me start all over again ! and here are the next steps:
Assume you want to generate for many apps: “Generate app password”
STEP 4 : LET’S use the multi-factor authentication that is going to send me a text message:
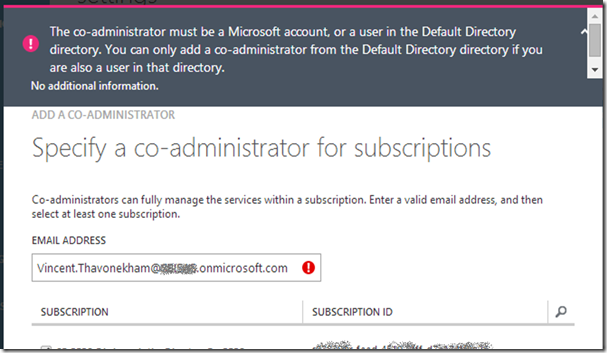
Add your new AAD user as a co-administrator (see potential error messages)
log-out, and sign in with this new co-administrator, with the temporary password previously generated.
Enter the code sent to your mobile phone… then tada ! you start to log into your application with your new MFA !
THAT’S ALL ! Now you can clean up all Microsoft Account (LiveID) so that ONLY people managed in AAD (with all advantages) could connect your Azure developer Portal.
============== T H E E N D ==============
============== A P P E N D I C E S ==============
More information here: http://technet.microsoft.com/library/en-us/dn249471 APPENDIX1 : Windows Azure MFA portal (formally PhoneFactor)
Where you could administer and configure the MFA. For instance here you could see a report that can be downloaded.or download the SDK corresponding to your programming language.
ALTERNATIVES: OLD FASHION RSA-SecurID way
MFA supports token sent to your mobile phone. You could also use alternatively the "old fashion" way, if you want to secure via VPN and securID,
you could set-up a Azure VM protected by VPN, where have stored the login/password of your Web Application in the browser, or better in a secured safe.
Note : you could change the Global administrator of your Microsoft Azure
============== S O M E E R R O R M E S S A G E S ==============
Setting up AAD-MFA for Azure Administrators is relatively straight forward Joy of some errors:
https://activedirectory.windowsazure.com/Interrupts/SignInAccessDenied.aspx
Some links on a given user may result in this:




































No comments:
Post a Comment
Note: Only a member of this blog may post a comment.